Mobile Threats – What Stays in Your Mobile Without Your Permission
By Patrick Robinson
January 10, 2024 • Fact checked by Dumb Little Man

‘Dog is man’s best friend’, said a man who doesn’t own a smartphone.
A lot has changed since the arrival of technology in the form of personal computers. People no longer associate technology to work but is by far one of the most equivocally loved forms of entertainment.
Since the first-ever iPhone launched in the year 2007, smartphones have been enriching human lives in ways more than one. Be it for staying in touch with your friends and family, accessing social media, exploring the world of information or for accomplishing work-related tasks, this handy piece of technology is man’s go-to device.
According to a study, 70% of employees use their smartphones within their office environment and 71% spend over two hours a week to access company information on the phone.
Our phones are our constant companions, whether we like it or not.
The number of unique mobile users today stands at around 3.5 billion, which is around 45% of the world’s population. Clearly, mobile phones, their optimal use and security are longer topics of concern for tech leaders and innovators.
And while as users we are very aware and active about mitigating the security risks on our computers, the same does not apply for mobile phones. Mobile security is taken lightly when compared to desktops and PCs and here’s why that is not safe!
Imagine having a home that stores all your possessions, material or otherwise. Your memories, your personal moments with your loved ones, a chest of drawers that has all your financial account details and also your work documents – all there.
Now imagine having an unknown guest or intruder that stays within your home without your permission. The said intruder has access to all your possessions.
Sounds scary, right?
Now, think of your mobile phone – it possibly has more personal possessions than your home. This includes:
- Your memories captured in the form of photos and videos
- Your private conversations in your messaging apps and emails
- Your banking apps and wallets
- Your work emails and resources
Your smartphones clearly cannot afford to have an intruder, at least not the one you didn’t invite in. But without having a mobile security policy in place, chances are, the uninvited guest is already here!
Types of mobile threats: Who this intruder really is
Malicious apps
These intruders come in from apps that you installed on your phone without thoroughly reading the permissions it asked for.
Apps downloaded from third-party app stores
These visitors tip-toe into your phone via the apps downloaded from third-party app stores. According to a report by Symantec, third-party app stores hosted 99.9 percent of discovered mobile malware.
Spyware
Walking into your phone through a link you clicked on some app or a website
Unknown Wi-Fi
The ones that clawed their way in when you connected to a Wi-Fi in a park or a cafe. 1 in 5 of the cyber attacks occur because employees connect devices to public Wi-Fi, either at cafes or elsewhere.
Inactive apps
The ones creeping up from an app that you once downloaded, rarely used but forgot to uninstall from your phone
Phishing
These intruders came announced, luring you into a great deal on your email or SMS.
How impactful are these intruders? Should I be worried?
These intruders are pretty powerful and according to a study by Juniper Research, the cybercriminals will steal more than 33 billion data records in the year 2023. The average cost of a data breach will exceed a staggering of 150 million USD by 2020. These intruders are clearly not guests you can take lightly.
The good news is that…
And 95% of cybersecurity breaches are due to human error which means that you can control the entry of these intruders by simply being aware, on a personal level. Along with creating awareness for security on a personal level, you can also protect your personal information by building a culture of security and implementing MTD – mobile threat defense. MTD can help in combating these intruders on your mobiles.
See Also: How To Secure Mobile Data: Tips to Protect Yourself Online
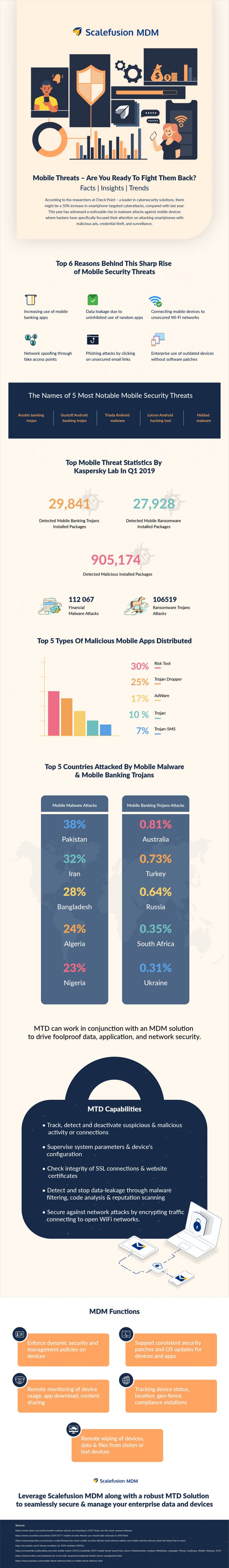
You can check out this infographic that details several insights into mobile threats and also have a glimpse into how mobile threat defense helps.
Source : scalefusion.com